Enumerate Harder!
My Motivation
For the past 5 years I have been wanting to start the highly recognizable course associated with the industry recognized Offensive Security Certified Professional (OSCP), but never felt I was ready. Several years ago the course was known as Pentesting with Backtrack, now its called Pentesting with Kali (PWK). There was never a good time to start this course, work was always crazy, I got married and started a family, job changes, moved, and of course I didn’t want to fail. The list went on and on and I constantly put it off, I think a large part of it was I felt completely intimidated and unprepared for something as challenging as the PWK course and the OSCP exam.
That all changed with my New Years goals for 2018, in February 2018 I started my OSCP journey with a 90 days access to the PWK labs, course, and certification attempt. I was under immense pressure to get this finished in under 90 days. Right around 92 days is when my wife was due, and I would be very busy with my infant son. Little did I know I would eventually fail my first exam and continue my journey while having even less sleep helping with night feedings.
Previous Experience
I’ve been in the IT / Cyber Security field since 2009, even longer if you count time at Geek Squad. Yeah Geek Squad, I know snicker but it was a hell of a fun experience thru college and a bit after. I held the prestigious positions of Counter Intelligence Agent (CIA), Double Agent (DA), and even Deputy of Counter Intelligence (DCI). More recently I’ve held jobs such as help desk, systems administrator, database admin, firewall administrator, and network analyst. So arguably, nearly ten years of experience in the field. I’ve taken numerous technical courses centered around penetration testing and digital forensics, and have participated in SANS NetWars CTF’s, and HackTheBox.
Over my work history, trainings, and personal interests I have had a lot of exposure to the following tech and skillsets which greatly helped me in my journey as well:
- Windows OS’s
- Linux OS’s
- Bash and Windows CMD line
- Virtualization
- Firewalls (McAfee Host Based, MikroTik, pfSense, etc)
- Networking (VLans, DHCP, DNS, TCP/IP, Routers, Switches, etc)
- Python Scripting
I’ve always had a curious mind and usually pretty keen on picking up new skills and figuring out how things work, I tribute that one trait to my overall success. Of course a ruthless schedule and the motivation to earn the certification help greatly as well.
PWK Course Pre-Requisites
The PWK course calls for experience and knowledge of a few technical areas for students to be successful, what threw me for a long time was that Offensive Security calls this an Advanced Penetration testing course yet also foundational at the same time.
- A solid understanding of TCP/IP, networking, and reasonable Linux skills are required.
- Familiarity with Bash scripting along with basic Perl or Python is considered a plus.
Don’t be thrown by these pre-requisites, knowledge of scripting will definitely help you but no means is a requirement for success. Don’t get me wrong though, without at least some understanding of the components of even a basic python script you will be challenged in the lab environment. If you can follow along with a simple for loop or if statement you will be just fine.
The biggest thing you really need to prepare yourself for is the amount of time you will be investing, seriously have a conversation with your significant other, kids, family, dogs, etc and let them know your sorry in advance. The magic number from talking to several people who’ve passed is somewhere around 500 hours invested, give or take depending on experience. If you can’t dedicate at least 20 hours a week to studying, then re-arrange your schedule so you can make that work. You will thank yourself later for that!

PWK Course Thoughts
When you signup for the course, you will get links to download the course material. There is a 380 page PDF that contains the course material of all text, and hours of instructional video that match up with the course material. The PDF can be a bit dry at times, so I used that more as a reference guide and read the sections I felt the weakest in and skimmed the rest on my first pass of the material. The videos however are fantastic! I really enjoyed listening and watching the instructional videos on various advanced penetration testing techniques. The buffer overflow walkthrough video was very meticulous and easy to follow. I only watched it twice thru, by comparison I watched the eLearnSecurity buffer overflow technique video at least 30 times. Maybe it was just me being more junior when I took the eLearnSecurity course but I definitely felt the PWK videos were more easily to follow. I remember pretty vividly after watching all the videos through just so pumped to hit the labs! “HACK THE PLANET” from one of my favorite Hacker movies kept repeating in my head.
The exercises are pretty great if you are just starting out, and just following the exercises will get your feet wet in the labs. In fact, a lot of the excercises have direct walkthroughs of how to complete the tasks in the videos. You really can’t ask for an easier setup, it’s clear there was a lot of thought and energy put into the design of this course. As an added bonus, if you document at least 10 unique exploitation techniques on 10 different machines that could potentially be up to 5 bonus points on your certification attempt. I did this, but wow was it meticulous! I easily spent 30 hours completing all the exercises and putting them in the proper format for the bonus points. It’s still great practice though as you learn how to document your exploitation steps of a machine and put it in a penetration test report, something you will need to do for the exam report as well.
See what’s amazing about the entire PWK course and labs is the fact that its not designed to be a comprehensive course, see the labs all are designed to teach you unique lessons. Each of these boxes will present a new challenge and to tackle this challenge you will need to do A LOT of self-study and research. I spent hundreds of hours reading about technology, techniques, and methods that were not covered in the material. This is where I think the PWK course really shines, they provide the glue and foundations to get you started but it’s up to you to do the rest!
PWK Labs
The labs are by far the best part of the entire course, I spent hundreds of hours in this digital playground learning and practicing the techniques for which I had read and watched. There are fifty plus lab machines in 4 different virtual networks that range in difficulty from extremely easy with tools like Metasploit to frustratingly difficult. These machines will test your ability to not only comprehend the lessons taught in the videos and course PDF but also your research ability. Your ability to google will help tremendously here, there were a lot of new techniques, technologies, services, programs, etc that I had never used let alone heard of before. My ability to google the crap out of those things and look for technical write-ups, blogs, past security conference presentations, etc was key on rooting every single box in the labs.
Some tips to help you get the most out of the lab boxes:
- Consider when the machine you are working on was created, use your enumeration skills to identify the build date or most recently modified date that makes sense. If you are using an exploit that was created years after that target date, maybe there is more than one way on the box. Try to find all the ways to get initial access and privilege escalation, don’t just take the easy route.
- Perfect your documentation. I found from the 1st box I exploited to the last that my documentation steps increased drastically, which helped me write my exam report very quickly. I’ll outline my steps in a future post.
- Use a spreadsheet to keep track of your initial access, and privilege escalation exploits. You may draw correlation’s that will help you quickly size up boxes in the future.
- Track your hours spent, you will appreciate it later. Looking back I know exactly how many hours I put into this entire effort (459!). Google Spreadsheets is super handy for this. Don't go overboard, keep it basic and log hours you put in each day.
Final Thoughts
I spent 459 hours over 158 days to earn my OSCP certification. My OSCP journey was by far the most technically challenging, nerve wracking, and downright amazing experience of my career. I’m only upset with myself for not starting this sooner, I put it off for entirely to long. To put it short, I put in more study time and effort into this entire course and exam then both my Bachelors and Masters degrees combined!
The fine folks at Offensive Security will constantly remind you to “Try Harder”, and I agree you will need to try harder then you’ve ever tried before to get through the labs and the exam. Of course this doesn’t make you feel any better when you’ve hit a wall and can’t seem to think of a way around it.

We’ve all been there, well instead of just “Trying Harder” I have a little saying of my own I adopted in my journey. I’ve found that when I’m truly stuck on a way forward against a box, whether it was in the labs or the exam, I simply didn’t have all the information necessary. So in instances where you are hitting a wall, try to take a step back and think holistically on the purpose of the box and how it was designed to be used. You need to fully enumerate the machine, and that includes re-enumerating once you get an initial shell. So with that in mind, instead of just “Try Harder” try to “Enumerate Harder”.

Alternatives
If you don’t think you are ready for this course, I encourage you to just dive in anyway. Nobody is really ever ready for a course this demanding. If your still on the fence check out these alternatives:
eLearnSecurity Professional Penetration Tester
4,000 courses on udemy on Penetration Testing
The OSCP Exam
TL;DR: This will not include any spoilers, instead it will be on my experience with my two examinations.
Exam #1 – FAIL
I took my first attempt when I had 290 hours invested into the labs and studying, with 43 boxes in the labs rooted. It wasn’t enough! I started my exam at 9:00 AM, the hours leading up to it I was a nervous wreck. I normally wake up around 5AM and am at work by 6AM and this morning was no different so for several hours I couldn’t not think of the upcoming exam. I didn’t really know what to expect and thought I was prepared enough, I had 43 boxes in the labs down including machines in all 4 VLAN’s which I felt had given me pretty good exposure to multiple techniques across Windows and Linux.
I started with a box that had a clear process which I practiced extensively in the labs and had my first 25 points to my name within 90 minutes, was feeling great at the time! I kicked off scans on the rest of the machines and went to town on working on the other 25 pointer, after several hours in I had user level access! I pivoted to the 10 pointer machine and after another couple hours I had that rooted. This is exactly where I was stuck for hours on ends, by 2 AM after working thru the exam with little breaks I was completely fried. I went to bed to try to get a few quick hours, but couldn’t fall asleep right away and was just a hot mess. I woke back up around 5 AM and went back at until my exam ran out at 8:45 AM. I didn’t have enough points to pass, even with my lab bonus points document prepared and I was so exhausted and upset with myself. Needless to say a Twitter post I created made me feel a lot better. The support from this community is truly magical, so really I appreciate that! What I learned is a lot of people fail their first exam, some were even calling it a right of passage!
Wiping myself off the floor from that failure, I went had on the labs and re-examed several weeks later.
Exam #2 – SUCCESS
I took my second attempt when I had 443 (cool number!) hours invested into the labs, studying, and my previous exam attempt. At this point I had rooted 52 total boxes in the OSCP labs and an additional 12 from VHL. Additionally, I had completed the eCPPTv2 exam for some added practice. I felt much better going into this exam attempt than my previous. Not only that but I knew exactly what to expect from the style of exam boxes, how the lab panel worked, necessary screenshots, etc. I started this 2nd attempt at 1:00 PM, much different than my previous attempt. To help clear my head before the exam started since I was up around 5 AM anyway I took my wife and kids out for a big breakfast. No computers, phones, or tablets around and just enjoyed some family time was the trick I needed to not think about my pending doom.
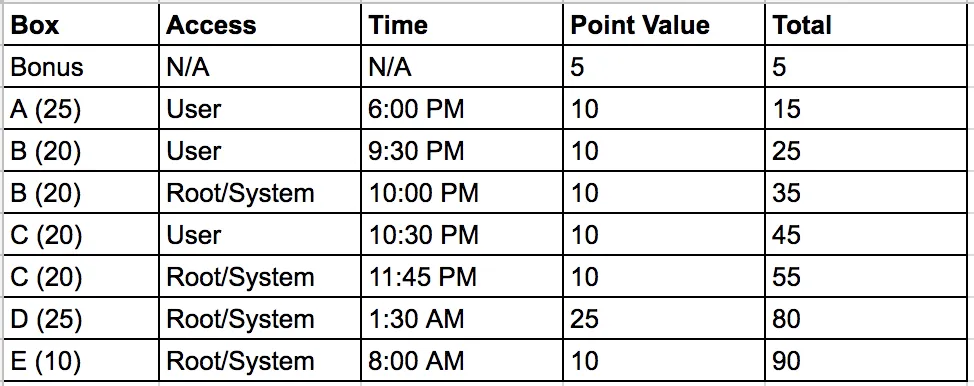
When the exam kicked off at 1:00 PM, I didn’t go after the same process-oriented box as I did last time. This time around I kicked off scans and started working on a box I picked randomly. A few hours in and I was still enumerating all of the boxes and was starting to feel I was wasting to much time, well the enumeration definitely paid off. I got initial shells and root/system on a few machines within a couple hours after that. In fact, by 1:30 AM just over 12 hours in, I had enough points to pass. I was feeling great at this point since I knew I had enough points to pass and had rooted 4 machines. At this point I went to bed and passed out quickly with a huge smile on my face. I woke up a few hours later feeling refreshed around 6:30 AM, got in a shower, some coffee, and quick breakfast and got to work on that last box. This final 10 pointer box didn’t take me to long and I had root/system level access to it by 8:00 AM! I was pretty satisfied with 4 roots and 1 user level access. I did try for several hours to root that final box but didn’t end up doing it, still I had about 85 or 90 points depending of OffSec counted my bonus lab points, well over the necessary 70 points to pass.
I kept a chart of my points and the time I gained access for reference: