Overall
Back in November 2017 I studied the Professional Penetration Tester (PTPv4) course from eLearnSecurity and took their certification the eLearnSecurity Certified Professional Penetration Tester (eCPPT) Gold. You can read all about my in-depth review of that course and certification on my blog post here
When eLearnSecurity announced they were releasing a new version of their popular course, I didn’t think about it much. I’ve been studying Offensive Security’s Pentesting with Kali (PWK) class with the goal of getting the OSCP certification soon for the past 3 months. I simply didn’t have the time to even think about studying more material, more labs, and another exam. However, when eLearnSecurity sent me a 60% off discount code since I was a previous student how could I say no! I looked into the course and the exam and found out there were two new main sections, 8 new labs, and a redesigned exam environment. Sounded like a perfect opportunity to practice my skills with buffer overflows and network pentesting at a cheap price.
Course Outline
There use to be three main sections of the PTP course (System Security, Network Security, and Web App Security), with the PTP v5 course eLS has added PowerShell for Pentesters and Linux Exploitation. The bonus sections were unchanged.
So with the addition of two sections, there are now four primary sections of the PTP course which teach the material that their Certified Professional Penetration Tester (eCPPTv2) exam is tested upon. Those are System, Network, WebApp Security, and Linux Exploitation. The new PowerShell for Pentesters, old Wi-Fi Security and Ruby for Pentesters sections teachings are not tested on their eCPPTv2 exam.
The three bonus sections all have excellent material and are great to read and study though. Their posted syllabus is quite extensive and breaks out each of these sections in elaborate detail, so if you really want to know if concepts are covered definitely check it out.
The two new sections that were added in PTPv5 course are PowerShell for Pentesters and Linux Exploitation.
- PowerShell for Pentesters
- Introduction
- PowerShell Fundamentals
- Offensive PowerShell
- Linux Exploitation
- Introduction
- Information Gathering
- Exploitation over the Network
- Post Exploitation
Labs
A lot of the labs are still the same, which I had a lot of fun with last year. I love how eLearnSecurity has a separate lab environment from other students and they give you a lab guide. The lab guide states the objectives and any info you may need, but at the very end they post the solutions walking you thru step by step. This is great for the novice student who is really stuck.
The following labs were new:
- Lab 11 - NBT-NS Poisoning and Exploitation with Responder
- Lab 17 - Finding and Exploiting DLL Hijacking Vulnerabilities
- Lab 19 - Leveraging PowerShell During Exploitation
- Lab 20 - PowerShell for Post-exploitation and Lateral Movement
- Lab 21 - Linux Exploitation - Remote Enumeration
- Lab 22 - Linux Exploitation – Local Enumeration
- Lab 23 - Linux Exploitation – Remote Exploitation and Post-Exploitation
- Lab 24 - Linux Exploitation – Lateral Movement
Course Interface
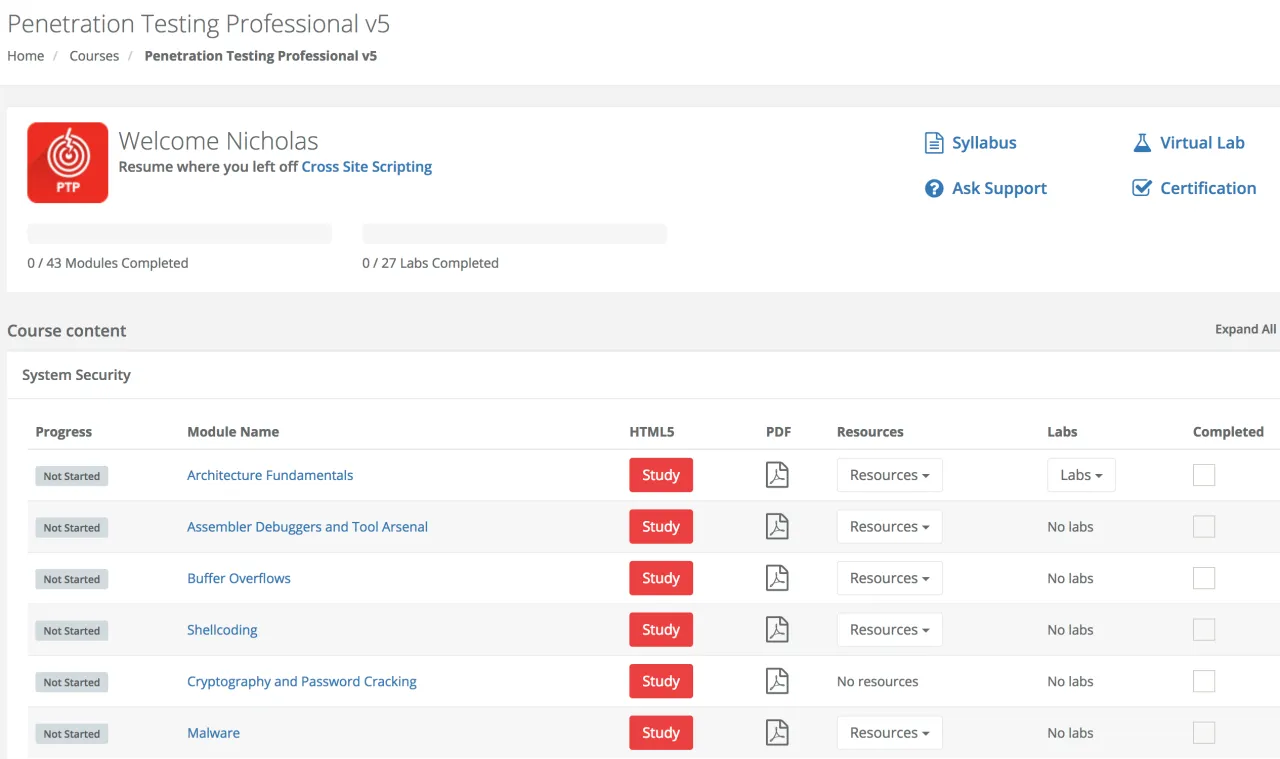
The course interface has been completely redesigned as well, it’s much easier to navigate and includes some nice new features. There are easy to navigate feature which launch study material in HTML5 format, no more clunky Flash! If you have the Elite version of the course there are quick links to the PDF materials too. Next to each module are also additional resources for that specific course module which link to the course videos. Next to that are any labs associated with that module. What I really like about this new user interface is the automatic progress traction when you use the HTML5 format. As you review the material it saves the slide you are on so you can quickly pick up later. There is also a checkbox for you to mark a section manually as complete.
Pricing
eLearnSecurity has raised their prices over the last couple of years with a big hike recently. Their are several different tiers of pricing depending on the level you purchase. I recommend the elite version, as this gives you double the lab training hours and ability to download the material in PDF format. Again, this is incredibly helpful for reference to digitally search through these documents and use as reference material on the fly.
Their prices range from $999 to $1,299 $1,199 to $1,599 and can be found below, they do offer pay as you go model.
https://www.elearnsecurity.com/course/penetration_testing/enroll
Exam / Certification
eLearnSecurity Certified Professional Penetration Tester v2 (eCPPTv2)
I’m not going to go into great detail on the exam for obvious reasons, but I will say I’m extremely happy it was redesigned. Overall, the exam was much more challenging then the previous version. I was happy that they graded my attempt in under 5 days, comparatively it took them 28 business days on the old exam.
Back in November 2017 I took the previous version of this certification, eLearnSecurity Certified Professional Penetration Tester (eCPPT) Gold. With version 5 of the Professional Penetration Tester (PTP) course, just like the course the exam has been completely redesigned! This was the only reason I decided to purchase the new course and get a certification voucher.
Since I had taken their old exam just 6 months ago, I still had it somewhat fresh in my head and of course had all my notes and exam pentest report write-up. After quickly reviewing the Linux Exploitation material, and do I mean quickly! I tore thru those slides in less than 10 minutes. I started the exam the night I got access to the new course. I finished the entire exam in two days for a total of about 3 hours. Again, that may not be everyone but over the past 4 months I’ve put in nearly 400 hours of study time into Offensive Security’s OSCP course and have rooted 51 boxes in their lab environment. I’ve even attempted one shot at the OSCP exam, failed with 55 points. So 3 hours may seem fast but its not when you put it in perspective of all the practice I’ve had recently.
When I started the exam, I received an updated scope of engagement which had a very familiar scope to the last one. In fact, besides some updated graphics and formatting it was identical. I quickly started the exam environment, downloaded the OpenVPN files and connected. Manually editing my /etc/hosts file in Kali to map the domain name used in the test to a static IP in the environment (all per their instructions) was super easy. Within 5 minutes of starting I had connected and made all the necessary configurations leaving me staring at the face of the “foophonesels.com” webpage. I quickly noticed that the frontpage was different than the last exam and had a sigh of relief. For a moment I thought everything was going to be the same!
If you’ve taken the previous exam, you’ll notice a similar look and feel and same number of boxes you are charged with finding vulnerabilities and exploiting as a penetration tester. They will definitely test you on your linux exploitation abilities, and I was really happy for the practice. You will be tested on not only your ability to exploit a machine but also elevate your privileges to root / system. It may not be as simple as throwing MS08-067 one shot in Metasploit for straight to system goodness. There is definitely more thought necessary, but they give you plenty of ways to achieve your objectives. It doesn’t stop there though, proper post-exploitation is a must to pass this exam! Network pivoting through subnets that you can’t directly see from your attacker machine can be challenging as well, so be sure to read up on multiple techniques. I love to use sshuttle and ssh port forwarding as they are incredibly stable ways to route your shells, of course Meterpreter has a great pivot feature too.
After you’ve exploited a box and have gained root privileges, you may find artifacts left over some are intentional and some are not. I found it amusing that there was a well known and popular VM used in penetration testing that was re-purposed for an exam machine. It was clear there was a lot of things clean up, but there was a lot of artifacts still there too.
Tips for passing eCPPTv2
- Work through all the labs, to the point you can knock them out very fast and explain to yourself exactly what you did.
- As you work through the labs, practice taking screenshots and copying useful tool input and output for your report.
- Documentation is incredibly important, if you wait until the end to start you will likely be very frustrated and possibly run out of time.
- Export all of the course material into PDF format, this will allow you to search through the PDFs quickly incase you get stuck. Searching for keywords, phrases, tools, techniques and getting a fast refresher is extremely helpful.
- I built a Kali VM specifically for the exam, on my host machine I kept all my notes in Microsoft OneNote and utilized a share drive backed up to Google Drive.
- Recommend having a Windows 7 x86 based VM setup with Immunity Debugger on it, this will help immensely with your buffer overflow exploit development.
- A lot of the tool syntax, commands, etc I’ve grown to know but I do refer back to my own cheatsheet I created for reference.
The Notification
After eLS has graded your pentest report you will get an email letting you know if you passed or not. I actually got some decent feedback on this exam, my last one simply said “congratulations”. This time around I hit all the objective of the exam and the report showed that, however they said they would have liked to see screenshots and documentation supporting how I tested and built out the buffer overflow exploit. Screenshots showing me working in Immunity Debugger and things like Mona and finding bad characters.



