
Overall:
I had the opportunity to take SANS SEC542 Web Application Penetration Testing & Ethical Hacking during the SANS Cyber Defense Initiative (CDI) event in Washington D.C. this December with one of the course authors Eric Conrad. Eric absolutely killed it, and was one of the reasons I signed up for this particular course. I had heard he was a great speaker and had lots of relevant pentester tales from his own company doing just that. I was pleasantly surprised to see that Eric’s stories really made each day for me. Eric’s pentest stories brought the concepts he was lecturing to life and really showcased their relevancy for me. Plus, I enjoy learning from a firehouse and Eric being from Boston area was able to keep up with that pace! The overall 6-day course left a great impression on me, and would recommend it for anyone new to Web App pentesting. The CDI event of course added additional benefits such as night talks and access to sponsors for the swag run.
My Prior Experience:
I’ve had a lot of exposure to the different vulnerabilities discussed, techniques, methods, and tools this course reviewed from previous self-study, Masters courses, reading InfoSec books, watching YouTube videos from tech conferences, and taking free online courses. Want to self-study or prepare for this course beforehand? Be sure to check out cybrary.it
- Web App Pentesting Several Free Articles & How-To’s
- Web App Pentesting Free Course
- Cross-Site Scripting (XSS) 3-types Overview
- Web Security Fundamentals
- Full Exercises on Web Security via Hacksplaining
Day 1:
The first day was all about reconnaissance using active and passive methods for research and information gathering of the target. Some useful passive methods were discussed, however this is an entire course in itself using Open Source Intelligence or OSINT. Additional active methods were discussed as well such as DNS scans using a variety of different tools and methods. Some discussions were held on SSL/TLS ciphers and how to test for weak encryption. Finally, we ended the day with the famous Heartbleed vulnerability including how to identify it and exploit it. Overall, this was the most bland day that I had trouble diverting 100% of my attention to as I already knew most of it.
Day 2:
We really started getting into the fun stuff on the second day with a lot more hands on labs. Lots of command line tricks were discussed including netcat, nmap scanning tips, curl, grep, and bash scripting to aide in web application configuration testing. There was also heavy discussion on actively scanning hosts using Burp and ZAP spidering tools. One of my favorite labs was directory brute forcing, ages ago I used the now defunct DirBuster tool. Come to find out that the ZAP tool now includes that functionality called ZAP Force Browse. We also discussed alternative methods to recreate the same functionality with different wordlists, generators, and tools. One really useful wordlist generator is the ruby based Cewl tool by DigiNinja. Cewl crawls a website for text in HTML, Javascript, etc following links to a specified depth and generates unique words discovered. This is especially useful when trying to identify a possible password an employee may have used unique to that organization or company. We ended the day with a heavy discussion on the Shellshock vulnerability. We discussed ways to test for the critical vulnerability and how to exploit it running simple bash commands to a backdoor via meterpreter.
Day 3:
The third day was by far my favorite, as it was incredibly fast paced and heavily lab-centered. We started off getting into information leakage, username harvesting, and the fun stuff like local and remote file inclusion, command injection, and directory traversal. There were lots of lectures around identifying vulnerable forms for command injection, we even had a lab to to take advantage of this and initiate a reverse backdoor to our netcat listener. There were several discussions and labs centered around identifying what this type of traffic looks like on the wire using the TCPdump tool as well. We also discussed methods to create our own PHP shell using very simple syntax. The second half of the day was all about SQL injection (SQLi) discussing heavily why and how it works. There were numerous labs centered around crafting SQLi payloads manually and then using the tool sqlmap to aide in the process of dumping an entire database.
Day 4:
Javascript and Cross Site Scripting (XSS) vulnerabilities were lectured on the fourth day. There were several labs around identifying XSS bugs from simple XSS alerts to more crafty methods of harvesting cookies back to a remote user. My favorite part about this lecture was the multiple methods for “catching cookies” as in sending domain cookies of an exploited XSS domain’s vulnerable users cookies to a remote system. We looked at methods to do that via simple HTTP GET and POST requests as well as slightly more advanced methods like a PHP cookie catcher. No Web App course would be complete without mention of the BeEF framework. There was a lengthly lab on how to utilize BeEF to hook a browser and the different options available to the framework including integration with Metasploit.
Day 5:
The fifth day seemed to stagnate a lot, this day could probably use more work in the course design in my opinion. There was a great lecture on Cross Site Request Forgery (CRSF) attacks including how they actually work to tackling them in a lab environment. My favorite lab was the Mobile man in the middle (MITM) attack scenario. Inside of VM we were given an Android emulator that had a custom “Bank” app which connected to a “server” that we ran locally via python script. The purpose of the lab was to showcase how you can use Burp Suite to capture outbound packets and manipulate them. In this scenario, we were able to modify the packets to send ourselves a bank transfer from someone else’s account. We could even manipulate the request to give us negative dollars which essentially added funds to our account since two negatives are a positive. The rest of the day seemed to jump around from how to use other methods when tools fail. We covered how to craft our own tools using Python and Bash scripts. To wrap the day up we went into using WordPress Scan (WPScan), w3af vulnerability scanner, and exploited a vulnerable website with the Metasploit exploiting Drupalgeddon.
Day 6:
Capture The Flag (CTF) Day. This by far was my favorite and probably where the real value in the course is. The CTF is laid out traditionally where groups of 2-5 people formed to tackle questions on a scoreboard. There were 4 levels in total. The first level was extremely easy, and were questions straight from the books on the first five days of lecture. These questions were more basic knowledge than anything else, most teams knocked these questions out in under 30 minutes. Level 2 started getting into more specific vulnerabilities such as heartbleed and shellshock as well as other reconnaissance methods discussed in the course. This was fairly easy since the question gives you the target server and what to basically look for, these were very specific and directed questions. Level 3 started getting more difficult, as the server is unknown. They gives you ranges or an IP address which is serving multiple virtual hosts (VHOST). The questions are all based on PII found on that particular server, you must find the server, identify the vulnerability, and then exploit it to gain access to an area which contains the PII to answer the questions. There were five questions here each worth 40 points and this is where a majority of the time was spent for the CTF. Section four is a freebie, if you successfully exploited all the servers in section 3 and properly collected the PII not just the PII in the questions then you could formulate a spreadsheet of the employee’s PII data. If you filled out the spreadsheet correctly, then the instructor gives you the “phrase that pays” which you enter into the one question in level four for additional points. You must use strategy, knowledge, understanding, and teamwork to win this CTF. All of the teams are extremely competitive and in our CTF we had several teams neck and neck the entire time. My team in particular just barely won by a few points in the last 5 minutes of the competition.
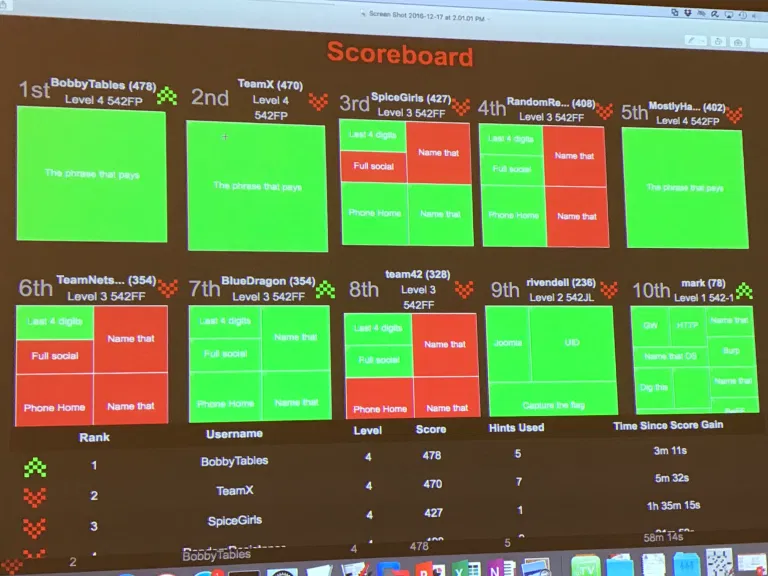

Suggestions to help in winning SEC542 CTF:
- Write out digital notes as you go through the 5 days of lecture. Be sure to write out tool syntax and a description of what it does.
- Pay close attention to the labs, they are used verbatim or slightly modified in the CTF.
- Take notes as you go through the CTF, record servers, IP addresses, methods used to exploit, usernames, passwords, etc.
- Be sure you coordinate with your teammates, you don’t want 5 people working on the same question.
- Absolutely finish level 3, even if you take some hints for reduced or zero points to finish the question. If you do this, you can fill out the PII spreadsheet and get 40+ points from that alone.
- Watch your time, it takes time to take the hints and submit answers, and record the results into the PII spreadsheet. It also takes time to show the instructor your PII document to get the phrase that pays.
- Craft the spreadsheet as you get the answers, don’t wait until the last minute.
Bonus! NetWars 2-Day Hacking Event at SANS CDI
Some of the bigger SANS events like the Cyber Defense Initiative offer a free add-on to your 6 day courses, 2 free nights of NetWars CTF focusing on hacking, forensics, and cmd line kung fu. The thing to remember about SANS NetWars is they are on about a 18 month rotation on their challenge questions. A lot of people competing at this NetWars have already seen a majority of the questions. A new feature to this years NetWars is the ability to form teams! A couple friends and I were able to form a team to tackle these challenges together. I consider myself very humbled to have placed on the leaderboard in position #10. There was some excellent competitors out of 300+ people in the room!
Suggestions to help in winning NetWars CTF:
- Brush up on your linux cmd line kung fu. Most of the questions in level 1 are just basic linux commands. Example: How do you identify what the “ls” command is aliased to? Or what kind of file is a specified file in the Downloads directory?
- Know how to google!
- Learn how to read through man pages and pipe to grep to quickly find what you need
- Work with your team, divide up questions and come together on the questions that require several questions deep.
- Don’t eat the nachos! IBS galore!


